Designing a Home Office That Boosts Focus and Comfort

Working from home has become a daily reality for many, making a well-designed workspace more important than ever. A home office that balances comfort and productivity can change how you approach your workday. This guide walks through simple yet effective ways to create a space where focus and comfort coexist naturally. Creating a Space That […]
How to View Your Old Instagram Stories In 5 Steps

Instagram Stories offer a great way to share moments that may not need a permanent spot on your profile. But what happens after 24 hours pass and your Stories disappear from your public feed? Fortunately, Instagram has a handy feature that allows users to revisit their old Stories. Whether you’re feeling nostalgic or want to […]
How To Remove Collections on TikTok Collections: 5 Steps

In today’s fast-moving world of social media, organizing content is more important than ever, and TikTok has made it easier by allowing users to create Collections—custom folders where you can save your favorite videos. However, as your saved videos pile up, there may come a time when you’ll want to delete or reorganize your Collections. […]
Optimum Login: How to Access Your Optimum Account Easily and Securely
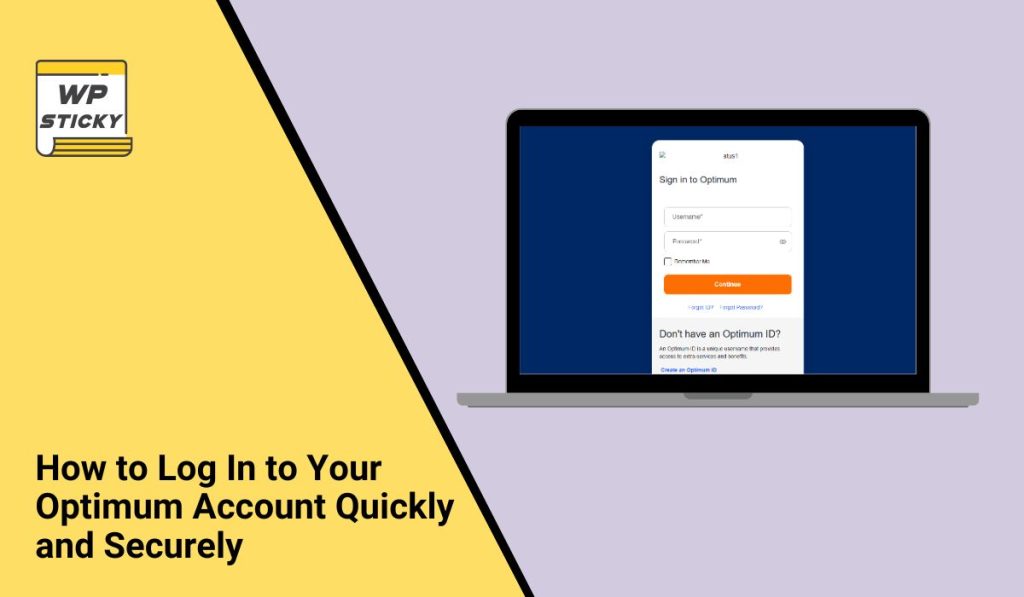
If you use Optimum for internet, TV, or mobile service, logging into your account helps you manage everything in one place. Whether you’re checking your bill, changing settings, or troubleshooting your service, the Optimum login page is your control center. Here’s how to sign in, fix common login problems, and keep your account safe. How to Log Into Your […]
Ivan Glasenberg: The Billionaire Leader Who Transformed Glencore

Ivan Glasenberg, a name synonymous with ambition and transformation in the global commodities business, helmed Glencore for nearly two decades and shaped it into one of the most powerful resource-trading giants in the world. With a reputation for being both enigmatic and fiercely intelligent, Glasenberg led the company through dramatic expansions, strategic mergers, and intense […]
Dominate Amazon: Rapidly Export Amazon Reviews for Ultimate Product Success

In today’s cutthroat e-commerce landscape, understanding customer sentiment can mean the difference between a product that flourishes and one that flops. Amazon, as the world’s largest online marketplace, holds a treasure trove of valuable user data in the form of product reviews. Learning to rapidly export Amazon reviews and analyze them strategically is essential for […]
How to Play AVI Files on Windows 10/11 [4 Ways]

If you’ve recently tried to open an AVI file on your Windows 10 or 11 PC only to encounter an error or blank screen, you’re not alone. While AVI (Audio Video Interleave) is one of the most popular video formats around, compatibility with modern Windows systems can sometimes be hit or miss. Fortunately, several reliable […]
How to Screenshot WhatsApp View Once | 5 Easy Ways

WhatsApp’s “View Once” feature has become a popular way to send self-destructing photos and videos. Once opened, these media files disappear and cannot be reopened, adding a layer of privacy for senders. However, there are legitimate reasons some users may want to take a screenshot of a View Once media, like keeping important information from […]
Best Event Booking Plugin for WordPress: Top 2025 Picks

In today’s digital age, managing events through your website has become a vital component for businesses, communities, and individuals alike. Whether you are organizing workshops, seminars, concerts, or appointments, a reliable WordPress scheduling plugin can make your life significantly easier. These plugins help automate the entire booking process — from accepting reservations and processing payments […]
Access Control Mistakes That Put Cloud Data At Risk

The fastest way into a cloud environment isn’t through a zero-day exploit or a brute-force attack. Instead, it’s through weak identity and access controls that let attackers simply walk in using valid credentials. Most breaches don’t begin with advanced tactics; they start with something as simple as a missing policy or a forgotten account. When […]
